From Chaos to Harmony
Centralizing Kubernetes Controller Upgrades


TL;DR: At Transmit Security, we developed a centralized system for upgrading Kubernetes DevOps controllers across multiple products and environments. Our solution combines GitHub Actions, custom Helm charts, and automated processes to streamline upgrades, enhance security, and improve consistency. This article details our approach, its implementation, and its real-world impact on our operations.
In the fast-paced world of Kubernetes orchestration, staying current with controller versions is not just a best practice — it's a necessity for maintaining robust, secure, and efficient infrastructure. Here at Transmit Security, where we manage a diverse portfolio of products across numerous Kubernetes clusters, this challenge is magnified by the scale and complexity of our operations. Today, we're pulling back the curtain on an innovative approach we've developed to centralize and streamline the upgrade process for Kubernetes DevOps controllers across our multiple products and environments, a solution born from the unique demands of our robust infrastructure.
Before we dive into our solution, let's paint a picture of the challenges we faced:
We needed a solution that would address these challenges while providing flexibility and control to our DevOps teams. Enter our centralized upgrade pipeline.

Managing Kubernetes assets can be so frustrating…
We've architected a comprehensive solution that harmonizes GitHub Actions, custom Helm charts, and automated processes into a streamlined upgrade symphony. Let's break down the key components and processes:

Devops-stack-charts: This is our maestro chart, conducting the orchestra of external charts. It contains:
This elegant structure empowers us to efficiently manage and customize resources for each controller while maintaining a centralized approach, significantly enhancing our operational efficiency.
Application-sets-chart: Think of this as our sheet music. It contains:
This chart is instrumental in our ability to manage configurations consistently across diverse products and environments, ensuring uniformity and reliability in our deployments.
renovate-scheduled.yaml: Our update scout. Running periodically, it:
This proactive approach ensures that our system consistently benefits from the latest controller versions, enhancing security and performance.
publish-chart.yaml: The Packaging and Publishing Maestro. It:
This process ensures that our customized charts are readily available for deployment, streamlining our infrastructure management.
generate-applicationset.yaml: Our template virtuoso. This action:
By ensuring that new configurations undergo review before implementation, it maintains the integrity of our infrastructure. This action triggers a script called get_target_repo.py that contains the mapping of a product name <> repository name and helps us understand to which repository should we open the PR.
apply-appset.yaml: This action is our deployment conductor. It:
Its role is pivotal in the bootstrapping process, as the ApplicationSet takes over the reins for automatic syncing post-deployment.
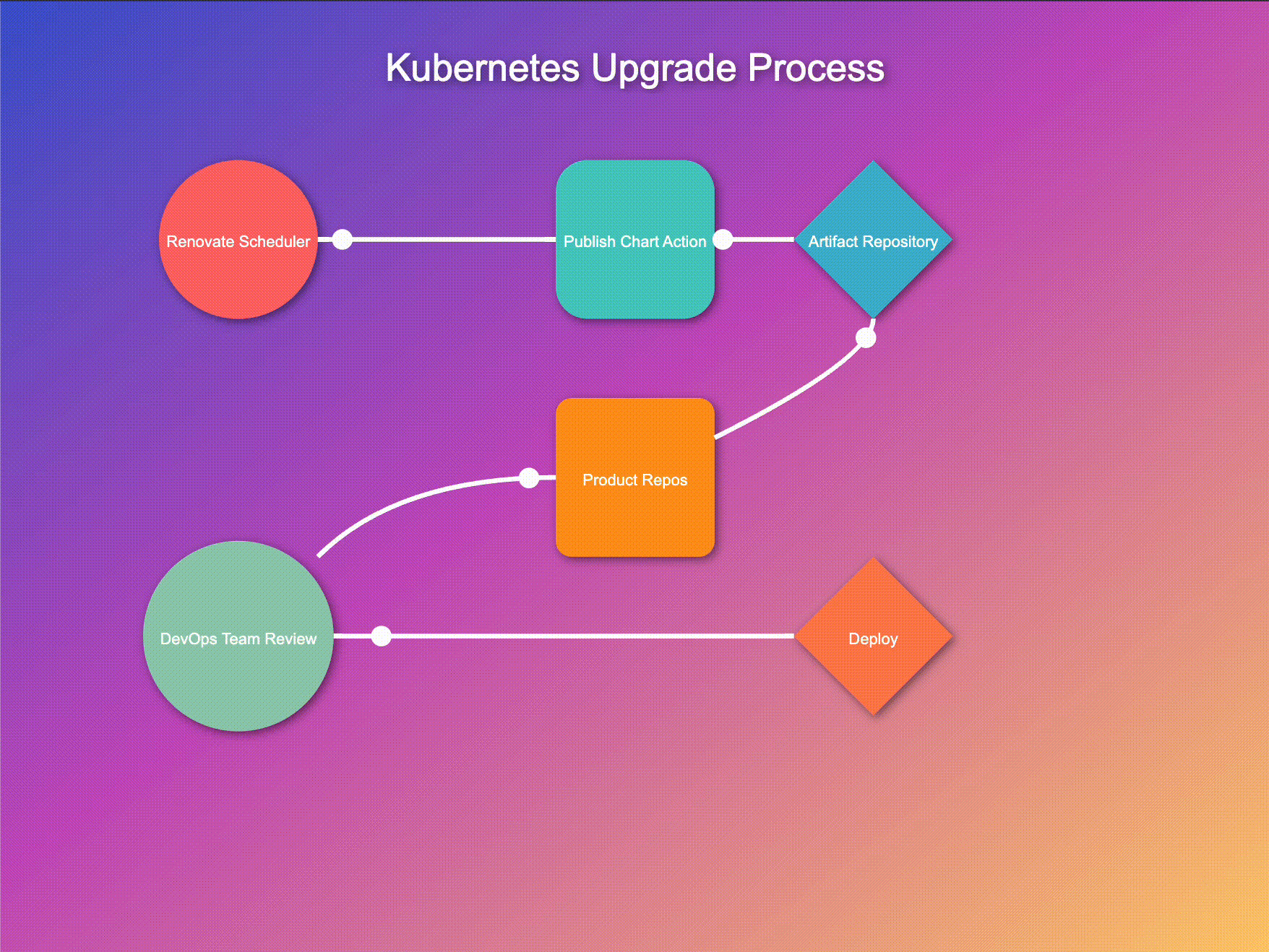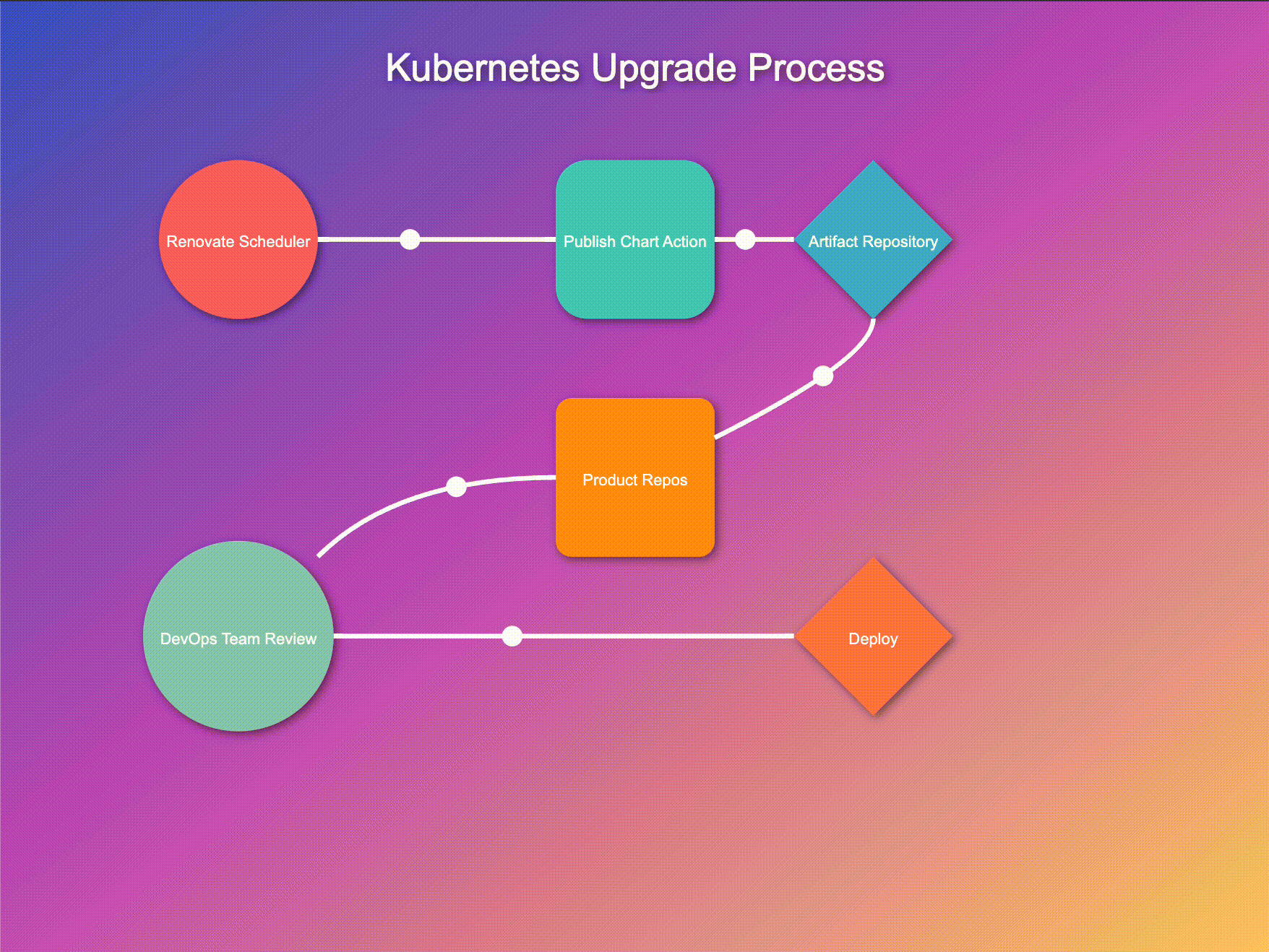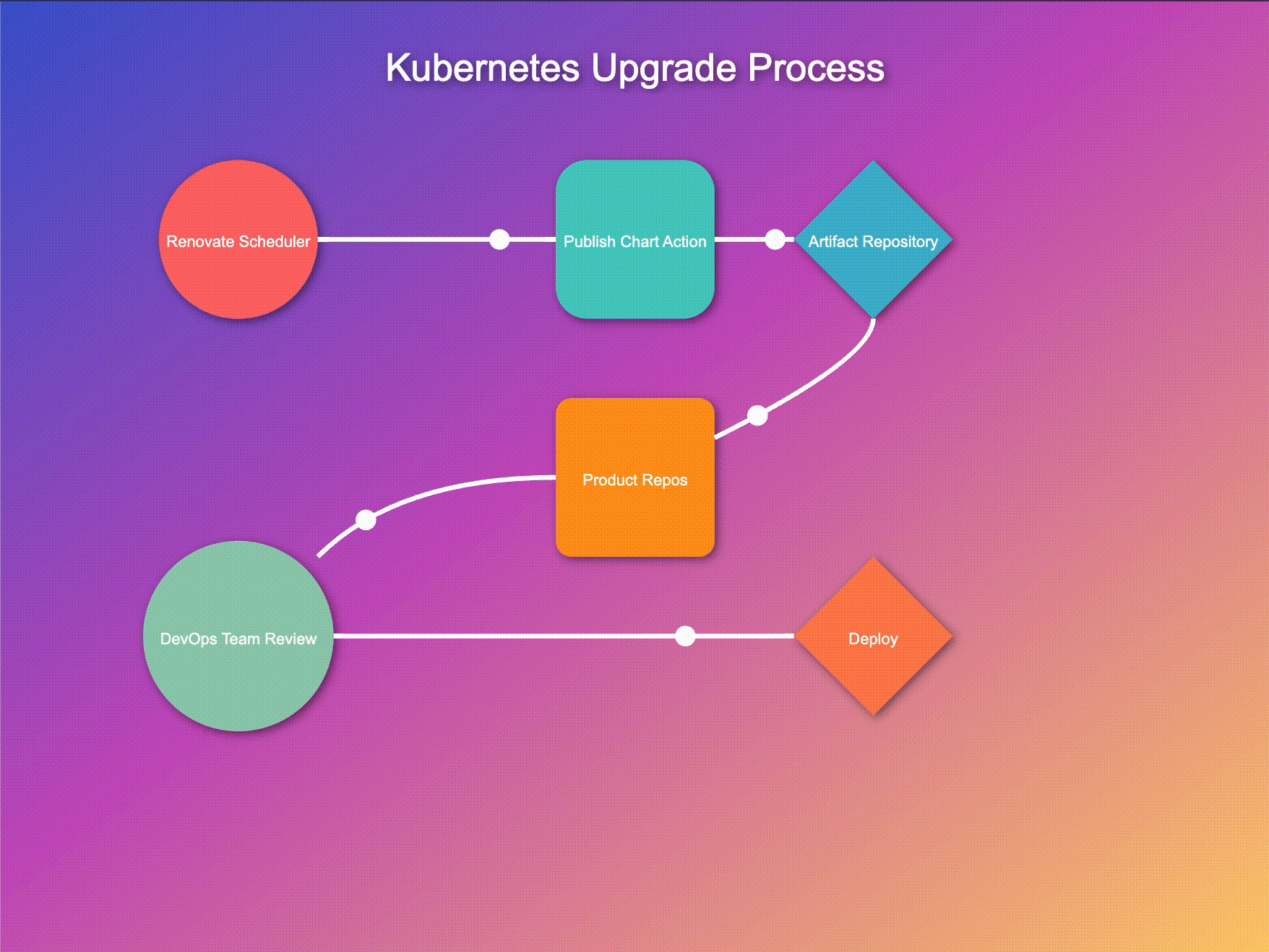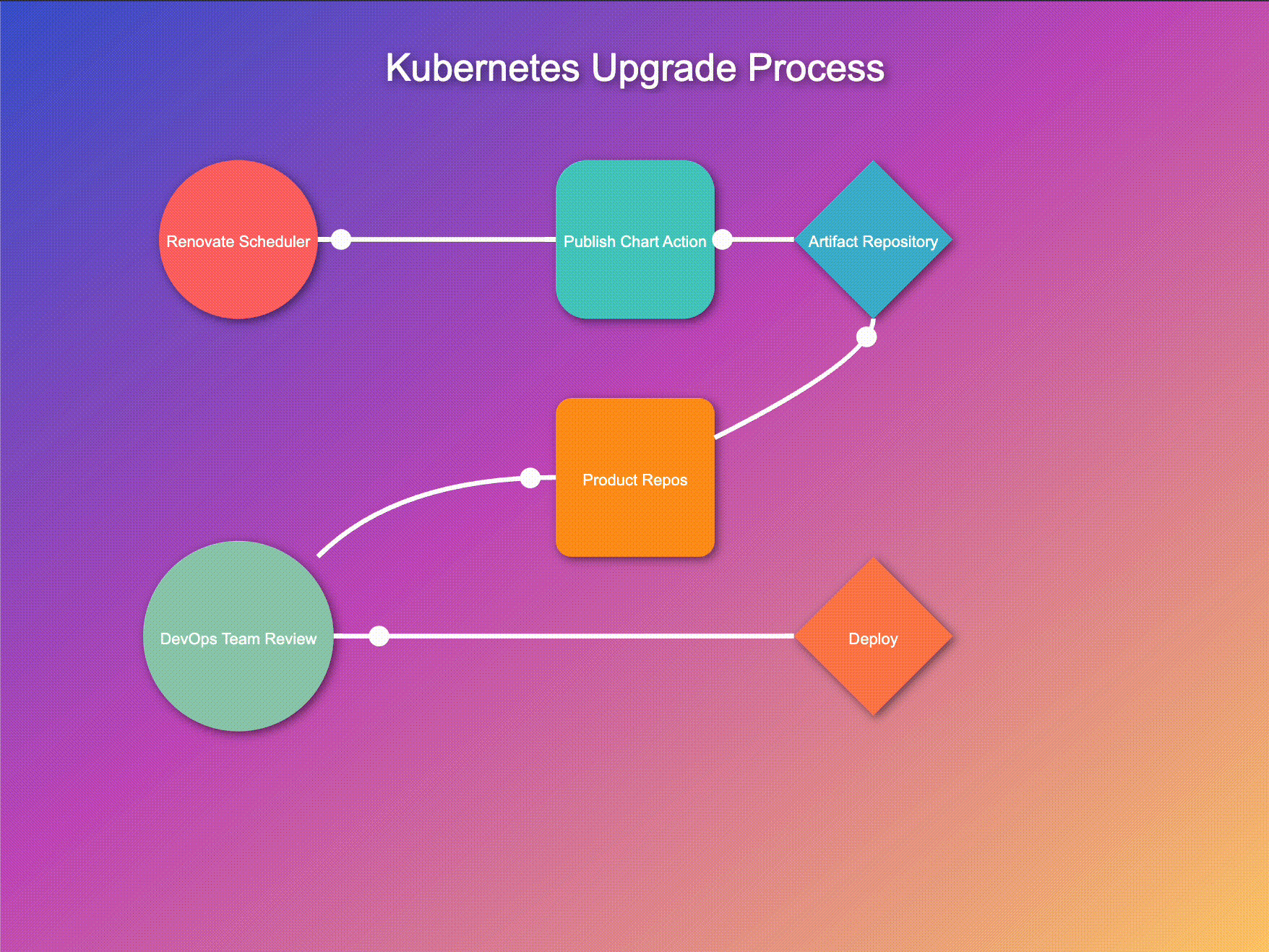
Let's walk through this process:
Periodically, our Renovate scheduler GitHub Action runs its reconnaissance mission, scouting for controller updates. This regular check ensures we're always aware of the latest versions available.
When Renovate detects updates, it triggers our publish-chart action. This process efficiently retrieves all charts from their repositories, unarchives them, and integrates our custom resources for each controller. The charts are then repackaged with these enhancements and published to our artifact repository. This streamlined approach ensures our deployment pipeline always has access to up-to-date, customized charts, ready for immediate use. By automating this process, we maintain consistency, reduce errors, and significantly improve our deployment efficiency.
As soon as new controller versions hit the artifact repository, our system kicks into high gear:
This automated PR creation serves as a proposal system, allowing teams to review changes before implementation.
While automation is at the heart of our system, we believe in the importance of human oversight:
This step ensures that despite the automation, humans remain in control of what goes into their systems.
After a successful deployment in the development environment, DevOps teams can confidently roll out the new version across other environments:
This process allows for a gradual, controlled rollout, enabling teams to monitor the impact at each stage.
A key aspect of our architecture is running a dedicated ArgoCD instance for each Kubernetes cluster. This approach offers several advantages:
This architecture aligns perfectly with our centralized controller upgrade strategy, allowing for granular control and monitoring of the upgrade process across our infrastructure.
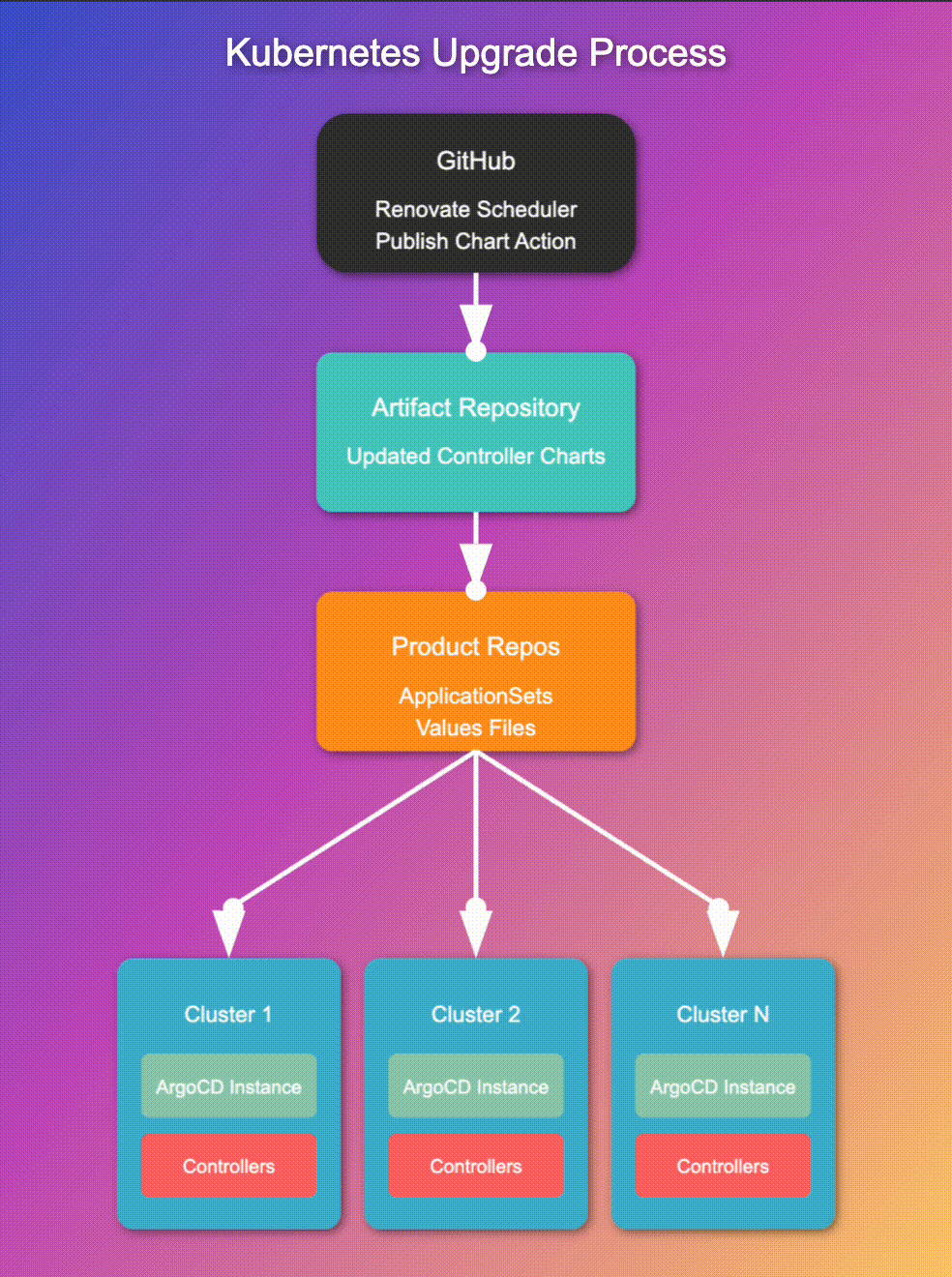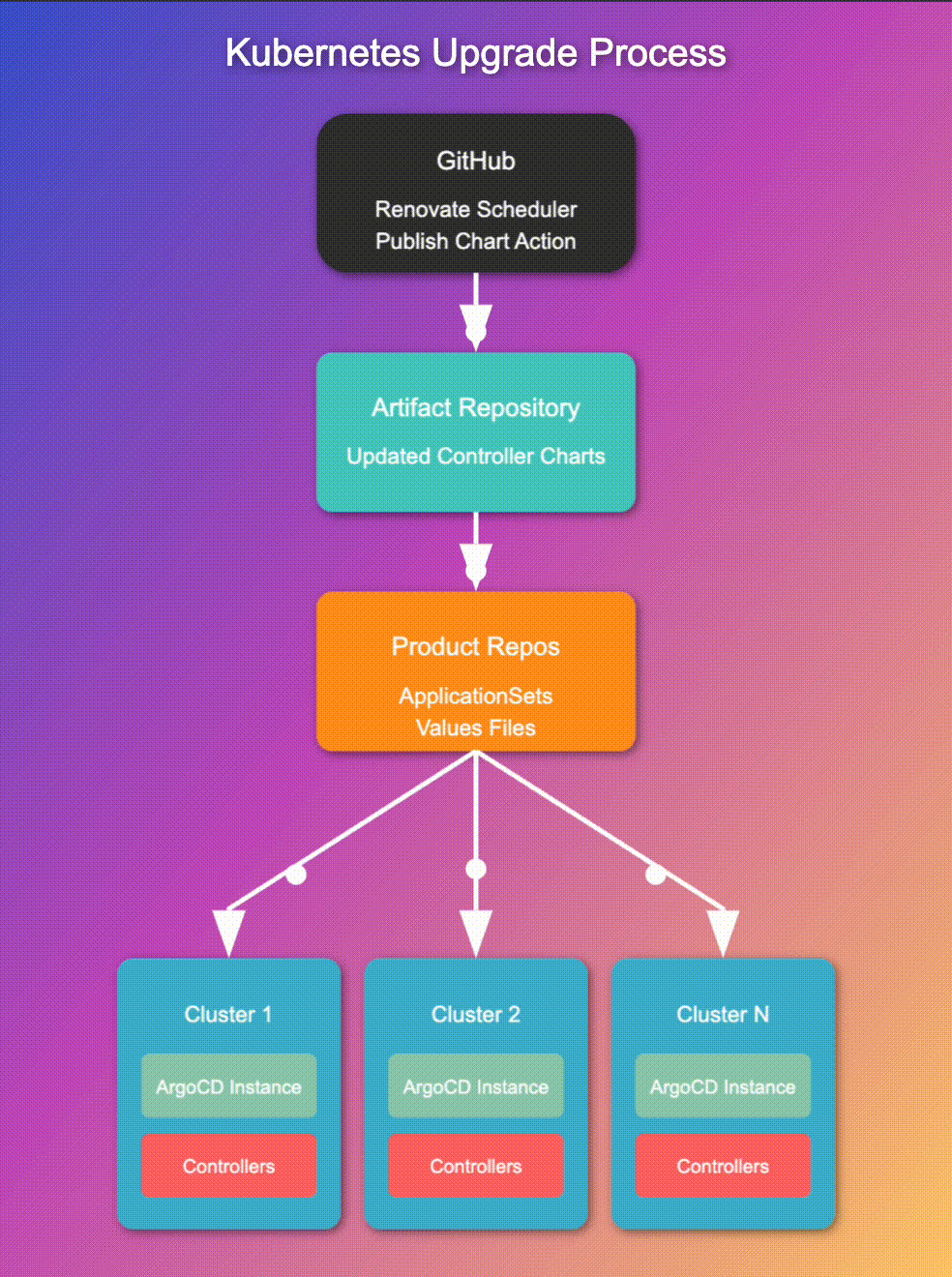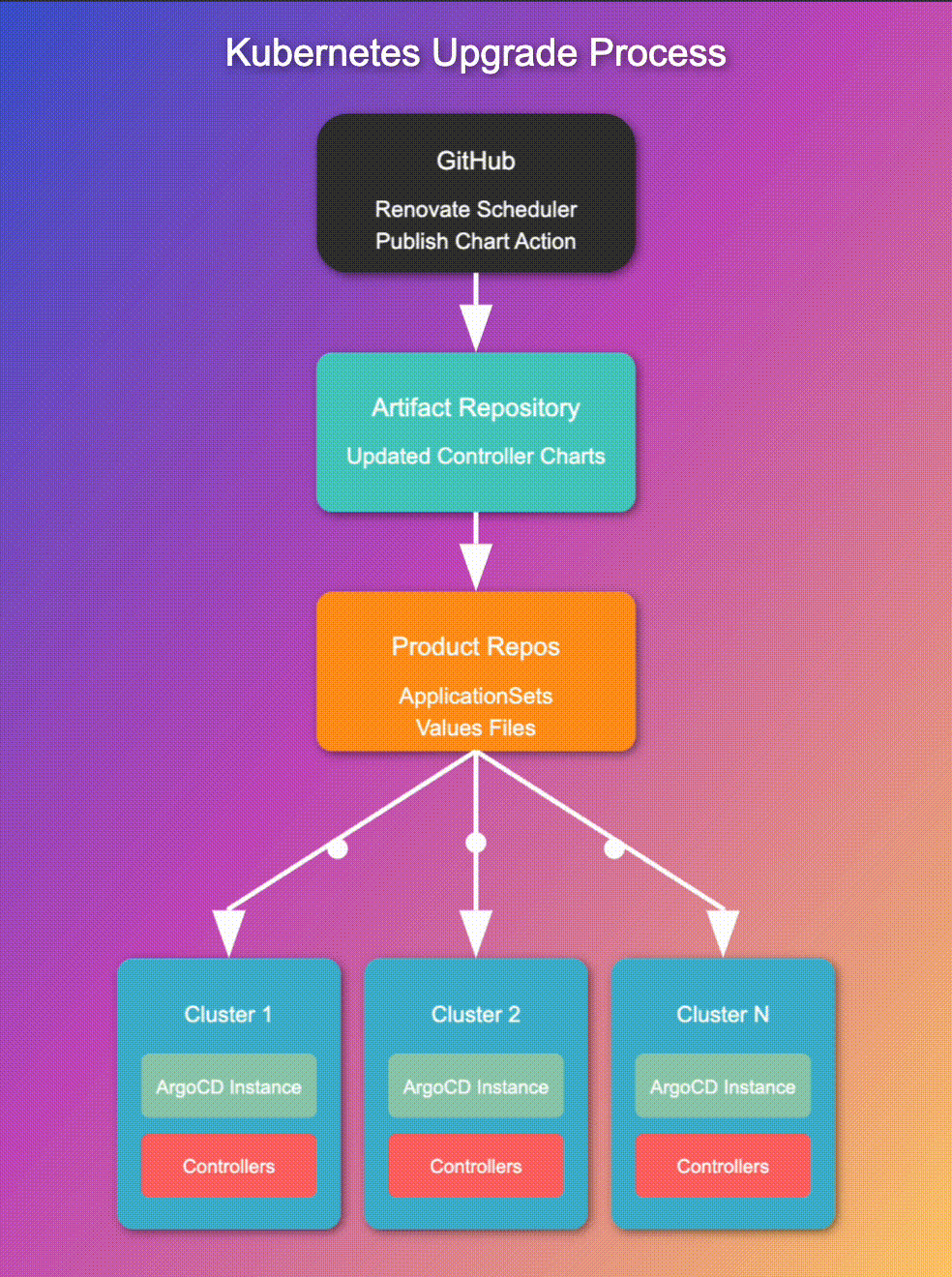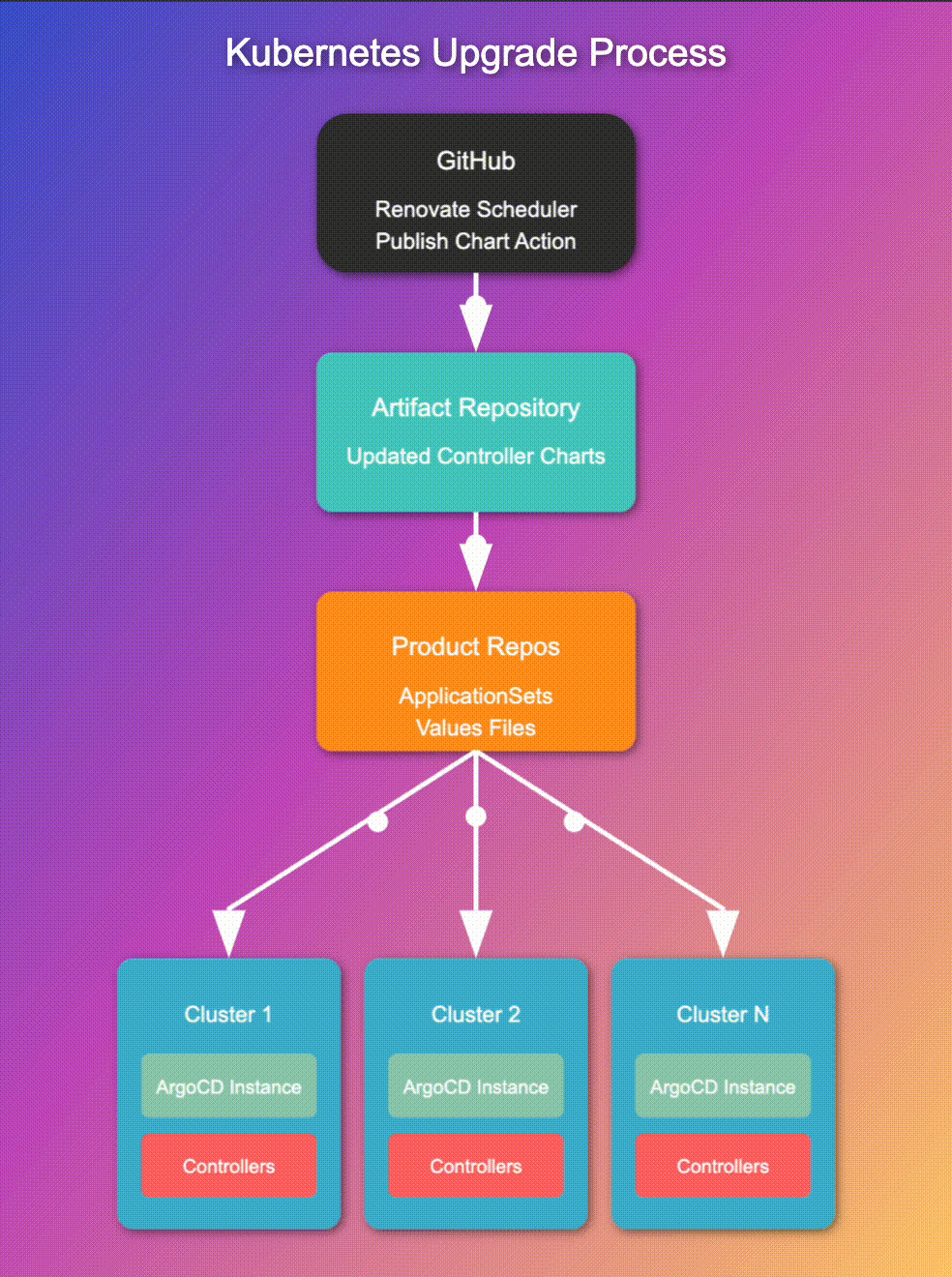
To give you a clearer picture of how our solution is organized, let's take a look at the structure of our per-product repositories:
This structure allows us to:
The applicationSet.yaml files in each cluster directory are the key to our centralized upgrade process, as they define which controller versions and configurations to apply to each cluster.
To illustrate the power of this approach, let's look at the following scenario:
When a critical security patch was released for one of our key controllers, our Renovate action picked it up. The publish-chart action immediately packaged and published the updated chart to the artifact repository. PRs were automatically created for our development environments across all products.
Our DevOps teams, alerted by Slack notifications, quickly reviewed and approved the changes. Within a day, the patch was tested and deployed across all development environments. Using the controlled rollout process, teams then systematically updated staging and production environments over the next maintenance time.
What once would have been a long, stress-filled scramble to manually update controllers across our entire infrastructure was reduced to a smooth process with minimal manual intervention.
By centralizing our Kubernetes DevOps controller upgrade process, we've not only streamlined our operations but also set the stage for more advanced automation and optimization in our Kubernetes ecosystem. This approach has transformed a once-cumbersome process into a streamlined, efficient operation that enhances our ability to maintain a cutting-edge, secure infrastructure.
As the Kubernetes landscape continues to evolve, so too will our processes and tools. By building a flexible, automated foundation, we're well-positioned to adapt to whatever challenges the future of container orchestration may bring.
I'm excited about the possibilities this centralized approach opens up and committed to continual refinement and innovation in our DevOps practices.